Demystifying the Security Debate Around Layer 2 Scaling Solutions
$GCR is a Tokenized Community of Researchers and Investors in the crypto space. Join our community today to get access to all the best investments ideas and deal flow, workshops and direct access to founders and key players in the space.
You will need 100 $GCR tokens to join the Discord members channel. You can purchase the token on Uniswap here and join the gated Discord group here.
Introduction
There has been a lot of debate recently around the level of security that Layer 2 scaling solutions on Ethereum provide to applications and users. This has brought on some confusion around side chains vs. rollups and how different scaling solutions interact with the Ethereum mainchain. In this report we take a look at what scaling solutions are, why they were created and the level of security that can be expected from each one.
Why are Scaling Solutions Needed?
To most in the community, the scalability problem is obvious. However, we have found that framing the question helps better frame the security debate. Below is a summary of the scalability / blockchain trilemma; those who are intimately familiar with this subject may choose to skip this section.
Most public consensus blockchains rely on a large number of nodes to validate transactions. This is what makes the network decentralized. Assuming the consensus mechanism is robust, once this network a sufficient number of validators, we can also think of it as secure. However, the fact that transactions must be verified by a large number of nodes leads to slow block times, and higher costs as demand for the network increases. For instance, Ethereum 1.0 can currently process ~15–18 transactions per second, while traditional non-decentralized comparables such as Visa can process ~24k tps.
This problem has persisted in the blockchain space since the very beginning, and is called the Blockchain or Scalability Trilemma, which states that a blockchain can only have two of the following three, because of the interplay between these factors: security, scalability, and decentralization.

Scalability solutions exist to help large, decentralized Layer 1 networks such as Ethereum grow without a fundamental compromise on decentralization or security.
How do Scaling Solutions Work?
Scaling solutions typically create a separate instance of the Layer 1 mainchain where transactions can be processed. The final state of these transactions can then be brought back onto the Layer 1 mainchain to verify. The key question is: how do these separate chains or instances address the scalability trilemma? Which of the three factors do these chains give up?
The solution is actually quite elegant. By enabling off-main-chain transactions, Layer 2 scaling solutions allow developers to choose their own tradeoff between speed/cost and security.
Consider the following analogy in money storage:
- Someone with $1 can put it in their pocket
- Someone with $1k can use a wallet
- Someone with $1M can use a secure online account
- Someone with $1B can use a triple-lock vault
Today, with Ethereum even $1 holders have to use a triple-lock vault, which is inefficient. Layer 2s optimize the system by allowing various applications to choose their own mix of speed and security. For example, and NFT platform could choose high speed +relatively low security, while a yield aggregator could use lower speed + higher security.
Another analogy would be airlines allowing passengers to choose between cost and comfort (economy vs. business vs. first class), thereby always running a profit-maximizing solution.
Simply put, Layer 2s don’t force developers to make a certain tradeoff, but rather allow them to choose, which optimizes the entire system.
Types of Scaling Solutions
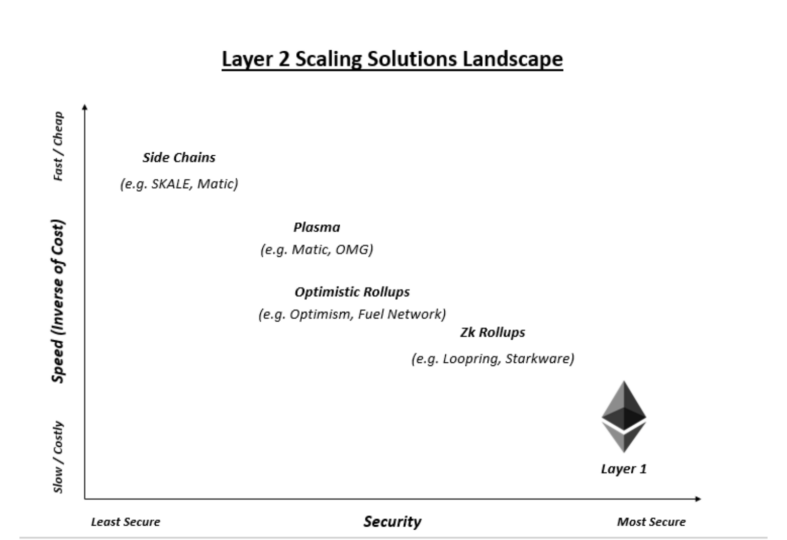
Naturally, each scaling solution does not in and of itself offer this optionality to users. Rather, each solution offers various mixes of speed/cost and security (similar to flights offering economy vs. business vs. first class). Developers may then choose their preferred solution depending on the purpose of their application. There are currently four solutions that are most widely used today: 1) side chains, 2) plasma, 3) optimistic rollups, 4) zk rollups. Here’s how they work
Side Chains
- Side channels run parallel to Ethereum main chain and have their own consensus mechanism and are connected to Ethereum mainnet via a bridge
- Because side chains have their own consensus mechanism, they do not inherit security from the Ethereum main chain
- These chains typically have fewer nodes than the Ethereum main chain, leading to relatively lower level of security and are ideal for low-security Tx’s such as NFTs
- Projects using side chains include SKALE, Matic, POA Network
Plasma
- Plasma can be thought of as a type of side chain, but with higher security levels
- The plasma chain achieves this by semi-regularly capturing a number of recent transactions in a single hash and exporting it to the Ethereum main chain
- The proof that is submitted along with each mainnet commit is the has function derived from a Merkle Tree, which is simply a combination of the hashes of each Tx in the block
- The security mechanism that makes plasma more secure is called fraud proof; once committed to the mainchain, Tx’s in the plasma block can be challenged for up to 7 days
- The key issue with plasma is that, in the event of a challenge, data cannot be instantly checked to verify; the entire block must be unrolled back to the side chain to check
- Some projects that use plasma are OMG, Matic, Gluon
Optimistic Rollups
- Optimistic rollups follow a similar process to plasma, with one key difference around data availability
- Specifically, in a rollup, the transaction data is rolled up when a batch is committed to the mainchain; this allows for easier and fast auditing of fraud proofs
- They are called optimistic rollups because, similar to plasma, the only proof presented is the hash of the Merkle root, which does not tell much
- Therefore, optimistic rollups also trade off moderate security for faster processing times
- Some projects building around optimistic rollups are Optimism and Fuel Network
ZK-Rollups
- ZK (or zero knowledge) rollups follow a similar concept to optimistic rollups, but take security more seriously
- Each bunched transaction committed to the mainchain comes with a corresponding SNARK (or zero knowledge) proof
- Unlike plasma and optimistic rollups, they will not be committed to the mainchain until the SNARK proof has been generated
- This makes it more secure, but also more expensive, given that SNARK proof generation is computationally heavy and requires more gas
- Ideal for platforms that host high value transactions (e.g. automated asset management)
- Some projects working on this include Loopring, Starkware, zkSync
This table by Matter Labs gives us a good idea of how these solutions stack up and the options that developers have when building for their projects.

Demystifying the Security Debate
The security debate is centered around the criticism of certain layer 2 scaling solutions for not being “secure enough.” Going back to our airlines analogy, this is similar to saying that economy seats are not viable because, despite being cheap, they are not comfortable enough. Eventually, having a mix of various tradeoffs is what optimizes utility of the underlying network. We are, of course, the first to admit that security on a blockchain is certainly more pressing a need than comfort on an airline. However, all solutions offer a base level of security that allows it to be operational with relatively trivial levels of security failure.
Eventually, claiming that one solution is the best or criticizing a solution for being less secure is a fool’s errand. Each solution can be optimal or not based on the underlying use case. Which is why these solutions are most powerful when being offered as a suite that developers can choose from.
-
check out METER.IO l2 plus multi bridge