Mapping The New Internet

We built GCR on the foundations of sound research and investments. So when a newsletter we thoroughly enjoy reading reached out, we were excited to collaborate. Decentralised.co is trusted by management at over 200 firms to stay updated on the trends, data and insights that matter. Sign up for their newsletter below—more on this collaboration for our most active members on Discord.
Identity helps scale economies. Commerce on the internet scaled when e-commerce enablers like eBay and Paypal embraced identification systems to reduce fraud and protect users. Web3 is at a similar juncture where it requires more sophisticated forms of identity to scale. The law and limitations of scaling platforms while capturing little to no data of users would require developers to tinker with new primitives that focus on identity.
Decentralsied.co’s latest post sets the stage for why and how identification on the internet has evolved over the last decade. It then sets the stage for the role blockchains play in identity verification. Read to understand the nature of applications enabling faster, more efficient systems of identity & the applications they could allow. The industry will have some hard decisions to make as trade-offs of privacy are made for convenience and scale in the next few years.
Few things before we begin.
1. This piece is written in the first person for easy reading. It would imply that I wrote all of this piece. But much of the groundwork was done by Siddharth. He has been the brains behind some of our best pieces. If you don’t follow him on Twitter already, you should.
2. Today’s piece begins with setting a baseline understanding of why reputation and identity matter online. We then look at how blockchain networks have historically maintained forms of reputation before understanding the primitives that power verification in the future.
With all of that out of the way, let’s dig in.
Remember July 1993? Me neither. I wasn’t born yet. Neither was Amazon, Alphabet (Google), Meta (Facebook) or X (Twitter). Much like blockchains today, the internet was a phenomenon that was slowly taking shape. The applications needed to onboard and retain users did not exist. Subscriptions to internet services plagued users because of how costly they were. It used to cost $5/hour. The technology was nascent and easy to write off.

The comic on the left was published that month by an artist who could not care any less about the technology. According to sources, he had an expiring internet subscription that cost a lot and a deadline to meet. That was all the context he had on the internet. But it captures the state of the technology at the time quite well. The mechanisms to verify identity and reduce bad behaviour did not exist yet.
Most emergent networks have this trend in common. It is rather hard to establish who engages with it during their early days. One of Steve Jobs’s earliest ventures was a device that allowed individuals to spoof identity on telephone networks.
The evolution of the internet required verifying the identities of individuals. Because the information superhighway (as Al Gore used to refer to it) was only valuable so long as it could enable commerce. And doing business in meaningful volumes requires knowing the details of your customers.
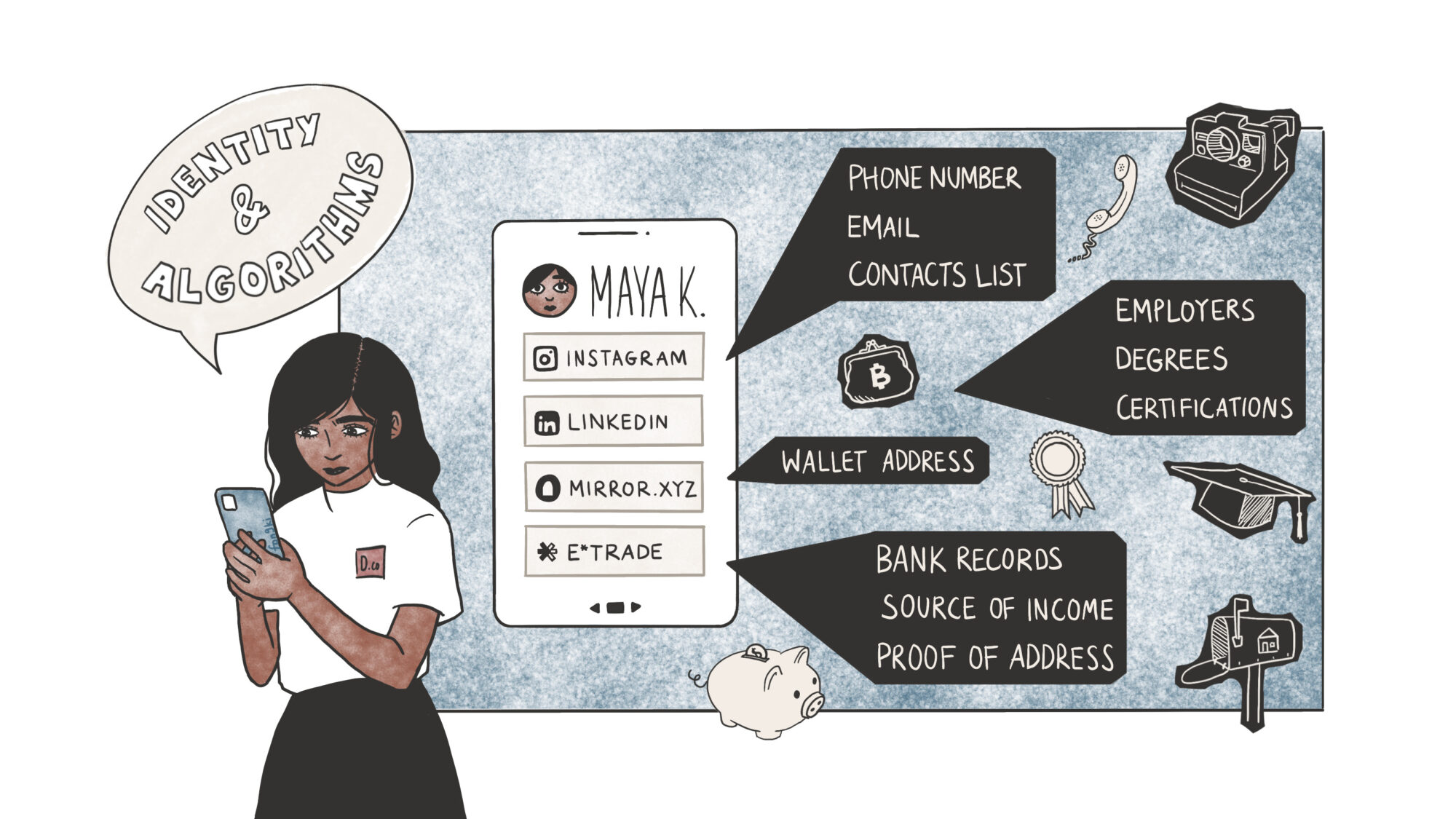
Purchasing on Amazon requires your address. Part of the reason PayPal agreed to an acquisition by eBay was the mounting fraud risks on the payments product. For the internet to evolve, trust became mandatory. Establishing trust requires knowing who you are interacting with.
Internet applications collect identity information according to the extent of consequences your actions may cause. It is a spectrum. A simple Google search requires only collecting your IP address. Emailing 100 people would need your email provider to have your phone number. Paying through PayPal would require handing over your state-issued personal identity documents. Regardless of where you stand regarding privacy, it is fair to suggest that applications can scale when the identities of the user base are established.
Large networks like the internet evolve when there is trust in the system. The emergence of different forms of identity instilled trust, and that has been the basis for a more secure, useful internet over the past decade.
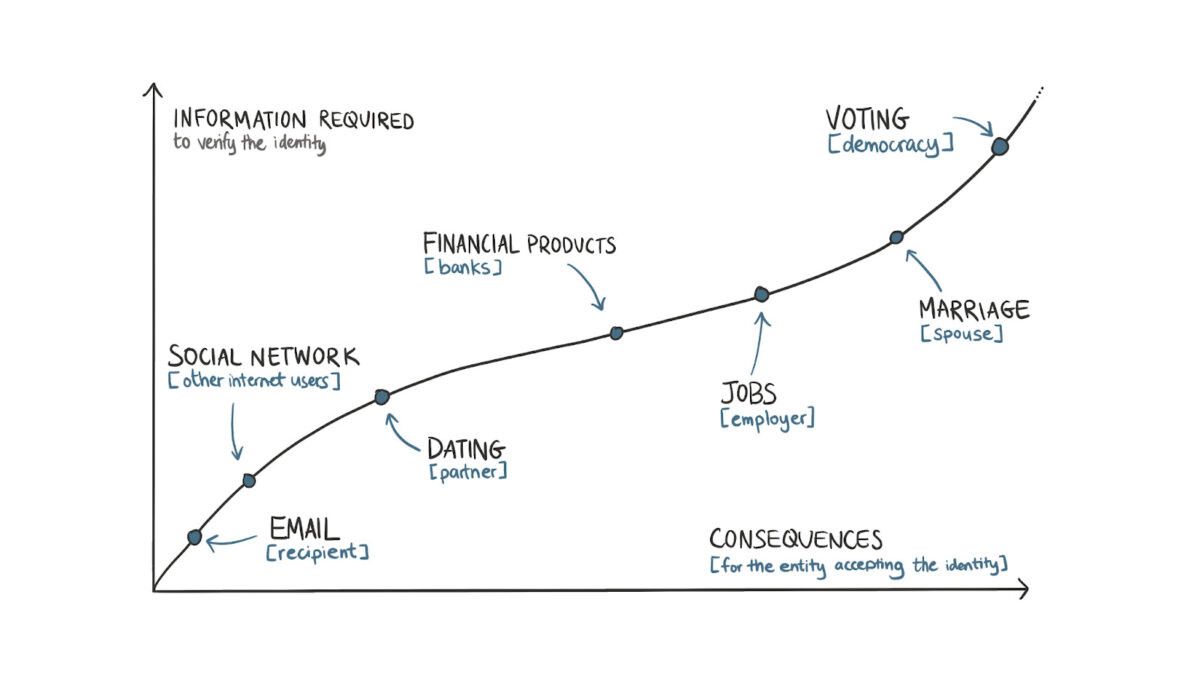
Seen through this lens, it becomes easier to understand why information gathered for each internet interaction is proportional to the possible consequences of one’s actions.
Accessing a social network only requires a person to submit their phone number. But for an account that is verified and has massive reach, the social network (like Twitter or Meta) may request additional forms of verification, such as a government-issued identity document. Similarly, banks ask for information on one’s employment and source of funds due to the possibility of an online account enabling illicit transactions.
At the absolute end of the spectrum is marriage (at the individual level) and a democracy (at a societal scale). Assuming rational actors (which is often not the case), people gather as much information as they can on a possible life partner before committing to wedlock. The identity of voters often undergoes multiple rounds of scrutiny, as a few thousand fake votes can tip an election to a person who may not be preferred.
Today’s piece explores a simple question: What happens when the forms of identity we use for blockchain applications can evolve? There are ethical considerations around why they should not evolve. Much of the industry is built on the ethos of relative anonymity and free access. But as with the internet, having additional context on users could be crucial for creating a new generation of applications.
There are two reasons why on-chain identity would become a necessity:
- Firstly, market incentives continue to drive individuals to exploit protocols through Sybil attacks. Restricting access to users relevant to an application helps improve the overall unit economics of businesses within the industry.
- Secondly, as applications become increasingly retail-oriented, regulations would require service providers to have additional information on their users. Placeholder’s Progressive Compliance article hints at this.
A simple heuristic to use here is that blockchains, at their core, are ledgers. They are global-scale Excel sheets. Identity products built on top of them are vlookups that filter specific wallets depending on the need of the time.
Networked Identities
The arrival of all new networks calls for the emergence of new identification systems. The passport emerged partly due to the rail networks connecting multiple European countries after World War I. We interact through fundamental identification units around us even when we don’t realize it.
A mobile device connected to a cellular device has an IMEI number. So, if you decide to make prank calls, the device’s owner could be traced by finding a receipt from when the device was sold. This is in addition to the fact that in most regions, acquiring a SIM card would also require some form of identification.
On the internet, if you use a static IP address, your details like name and address are already linked to your activities online. These are the primary identification blocks on the internet.
The single sign-on button solved one of the biggest hurdles on the web, creating a mechanism for applications to get details on a person’s identity without requiring them to fill them out each time. Developers could collect details such as age, email, location, past tweets and even future activity on a platform like X after collecting consent a single click. It collapsed the extent of friction in the onboarding process.
Several years later, Apple’s single sign-on button was released with deep integration into its operating system. Users can now share anonymous email addresses that do not divulge their details to the products they sign up for. What is common between all of them? A desire to know more about users with the least effort possible.
The more context an application (or social network) has on a user, the easier it becomes to upsell products to them with targeted identities. The basis for what we now call surveillance capitalism is the ease with which firms on the web today can capture users’ personal information. Unlike Apple or Google, blockchain native identity platforms have not scaled yet, as they do not have the kind of distribution those behemoths possess today.
Blockchain, native identity primitives, are unique because everyone can access user behaviour details. However, the tools needed to identify, track or reward users based on their past behaviour had not evolved until a few quarters back. More importantly, the products that tie on-chain identity to your real-life documentation, such as passport or phone number, have not scaled yet.
Part of the reason is that the products that require such use cases have not scaled yet. During the days of the ICO boom, Civic was often used to verify the identity of an individual purchasing tokens in a sale. Years later, they transitioned to checking identity on beer vending machines.
For the past few years, the primitives used for identifying users in our ecosystem have been wallet addresses, NFTs and, more recently, soulbound tokens. They serve similar functions as the IMEI number or IP address on the internet. Wallets can be spun up hundreds of times by the same individual, which takes a click of a button. They are similar to email addresses during the internet’s early phase. By some measure, in 2014, some 90% of all emails were spam, and one in 200 emails included a phishing link.
We have created elements of identity around a wallet address using its on-chain behaviour. Degenscore and Nansen’s categorisation of wallet labels are early instances of what these look like in practice. Both these products examine the historical activity on a wallet and issue a tag.
On Nansen, you can scan a token’s holders and find the number of ‘smart wallets’ that hold the token, the assumption being that the higher the number of ‘smart’ token holders a product has, the higher the probability of it rising in value as ‘smart money’ continues holding exposure to it.
NFTs became an instrument for identity through their scarcity. Some ‘blue-chip’ NFTs in 2021 were limited to several thousand mints. Bored Ape NFTs had a cap of 10,000 in total. These instruments became symbols of identity through their ability to verify one of two things:
- A person had access to ‘alpha’ by being early enough to a mint.
- Or they had the capital to buy an NFT in the market after the mint finished.
An NFT becomes a symbol of value by virtue of who else owns one. Bored Apes were once owned by Steve Aoki, Stephen Curry, Post Malone, Neymar and French Montana. The challenge with NFTs is that they are static in nature and owned by a community. An individual could have accomplished a considerable amount since a Bored Ape’s 2021 mint, but an NFT could show nothing to verify that.
Similarly, if a community develops a bad reputation, that seeps over to the holder of the NFT too. College degrees are similar to NFTs in that both can appreciate or depreciate depending on the actions of other parties involved in holding the instrument of identity. (In some cases, they are also similar in that their holders tend to hold remorse about the high prices at which they acquired the degree or NFTs.)
Vitalik Buterin proposed an alternative to the conundrum in his paper on soulbound tokens. Unlike NFTs, soulbound tokens (SBTs) are designed to be non-transferable and require a user to accept them. The crux of the concept is that issuers (like universities) could release tokens representing accreditation to wallets from which they cannot be moved. Other token holders from a similar accreditor could attest to the validity of an SBT.
So, if I claimed to work at McDonald’s and had an SBT issued to back the claim, a future employer could validate that claim far more quickly than by checking my LinkedIn or CV. I could further strengthen my claim if I had a group of colleagues attest to this claim on-chain with their SBTs. In such a model, my claim is verified by the issuer (McDonald’s) and through a network of attesters (colleagues) willing to back that claim with their on-chain identities.
Tokens and NFTs are similar in that they are acquirable proofs of status. An SBT’s being non-transferable means the wallet that owns it has accreditation that is usually earned
In the above example, a McDonald’s attestation may not be easily acquired by going to OpenSea.
But a Bored Ape NFT could be if I had the money to do so. What makes SBTs interesting is the possibility of mixing and matching them to create social graphs. We need to understand LinkedIn’s core value proposition to understand what I mean.
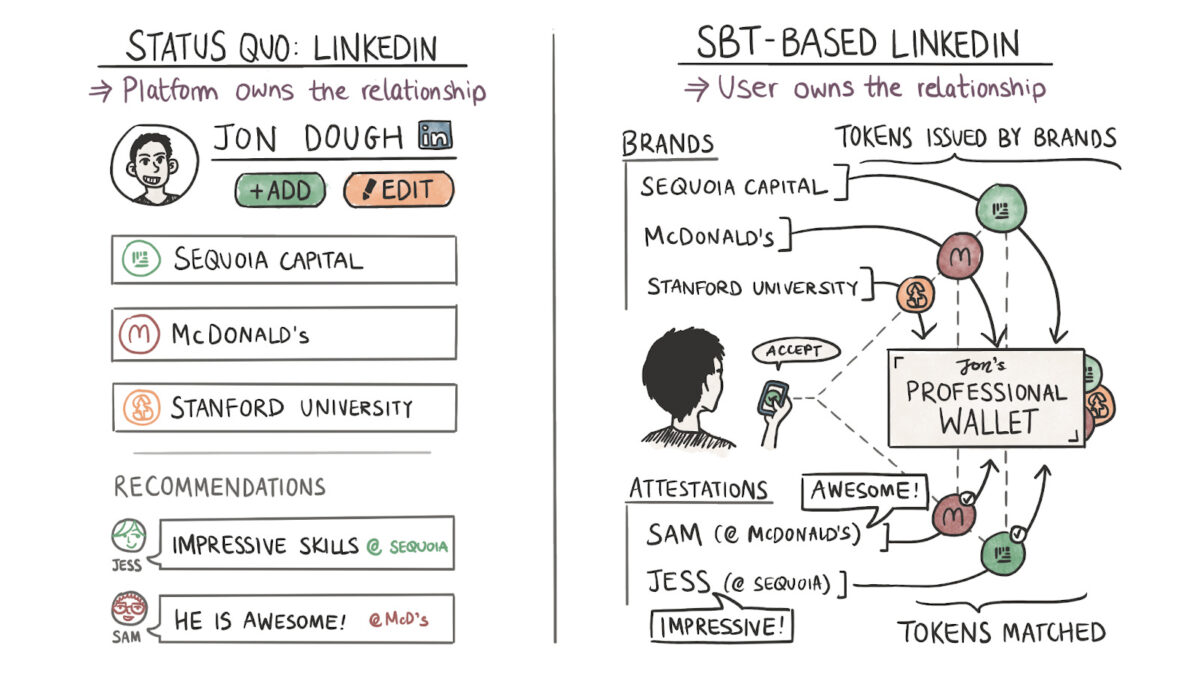
LinkedIn, like all social networks, offers status as a service. On its feed, people compete to be the ideal corporate man. The genius of LinkedIn was in being early enough to create social graphs of institutions. I could claim that I studied at Hogwarts with Harry Potter and Professor Dumbledore on the platform in a matter of clicks. The social graph emanated from institutions.
A person’s status on the social network depends on the reputation of the organisations they associate with and the relative rank they hold at the place.
In my hypothetical example, the “strength” of my reputation grows with each new organisation I tie my identity to. As long as the network of people within these institutions does great things, my reputation grows with it. It’s the reason why we see the PayPal mafia as so significant.
Why does any of this matter? Because today, there’s nothing stopping individuals from making false claims on LinkedIn. The social graph is not verifiable or attested, so much so that spies from sanctioned nation-states use it to target researchers.
A network of wallets holding SBTs could be a more decentralised and verifiable social graph. Hogwarts or McDonald’s could issue my credentials directly in the above example. SBTs remove the requirement of a platform middlemanning the relationship. Custom applications could be built by a third party querying these graphs, which adds to the value of these credentials.
Owning a Hogwarts SBT could mean I get invited to a local wizard conference. Or it could mean wands at a discount. But it hasn’t happened yet. And the reason for it boils down to the number of users. Let me explain using BAYC as an example.

A group of bored apes on the blockchain.
Web3’s great promise has been that open social graphs will empower the issuer to have a direct relationship with the owner of an accreditation. But we have that here already. The graph above from Arkham is a visual representation of all the owners of Bored Ape NFTs. But if you had to contact all of them, your best bet would be to export their wallet addresses and send them a text through something like Blockscan.
A more accessible alternative is to go through the social profiles of Bored Apes or their Discord, but it simply repeats the initial challenge we had with identity networks in the first place. Distributing anything through those networks involves centralisation and permission from the management at Bored Apes if you want to reach scale.
All of this brings back a core problem with on-chain identity networks. None of them have scaled enough to enable network effects yet. So despite having the theoretical mechanisms to create open, composable social graphs that validate users through tokens, wallets, and SBTs, no Web3-native social networks have retained users and grown yet.
The largest ‘verified’ social graph that exists today on-chain is that of Worldcoin. They claim to have over 2 million users on the network. That is barely 0.1% of users on a traditional Web2 social network like Facebook. Yes, I’m comparing apples to oranges here – but here’s the point. An identity network is only as strong as the number of participants with some identity that can be verified.
There is a bit of nuance to be added here. When we speak of “identity” online, it is a mix of things. If I were to break it down, it would be
- Identification – The core primitives that individually identify who you are. This could be your passport, driving license or university degree. They usually verify your age, skill and location-related parameters.
- Reputation – In the context of algorithms like the one on X, it is a tangible measure of an individual’s skill or ability. This is linked to the quality of a person’s content on social networks and the frequency with which an audience base responds to it. In the context of work, it is the graph of entities that pays an individual (or entity) over some time. Where identification is usually fixed at a given point in time, reputation evolves over some time.
- Social Graphs – Consider it the interlink between a person’s identity and reputation. An individual’s social graph depends on who interacts with them and at what frequency. Individuals with high reputations (or social rank) interacting frequently with an individual leads to a higher ranking on a social graph.
As we go through this article, I will use these terms interchangeably as the organizations solving for identification on the internet are not solely looking to validate your passport. Some of them are building portable social graphs. Others want to identify your behavior on-chain to assign it a score so developers can better identify their users.
As with most things, there is a spectrum of applications even within the realm of identity on the internet.
The Core Primitives
Though anonymity was part of the feature set in crypto, we have had identity checks at the periphery. The bits where on-chain money converts to fiat transfers (exchanges) have historically mandated collecting user information.
Exchanges are the largest existing graph of on-chain persona linked to personal identification documents. But it is unlikely that an exchange (like Coinbase) will roll out an identity-linked product as of today given the conflicts of interest such an action may provide.
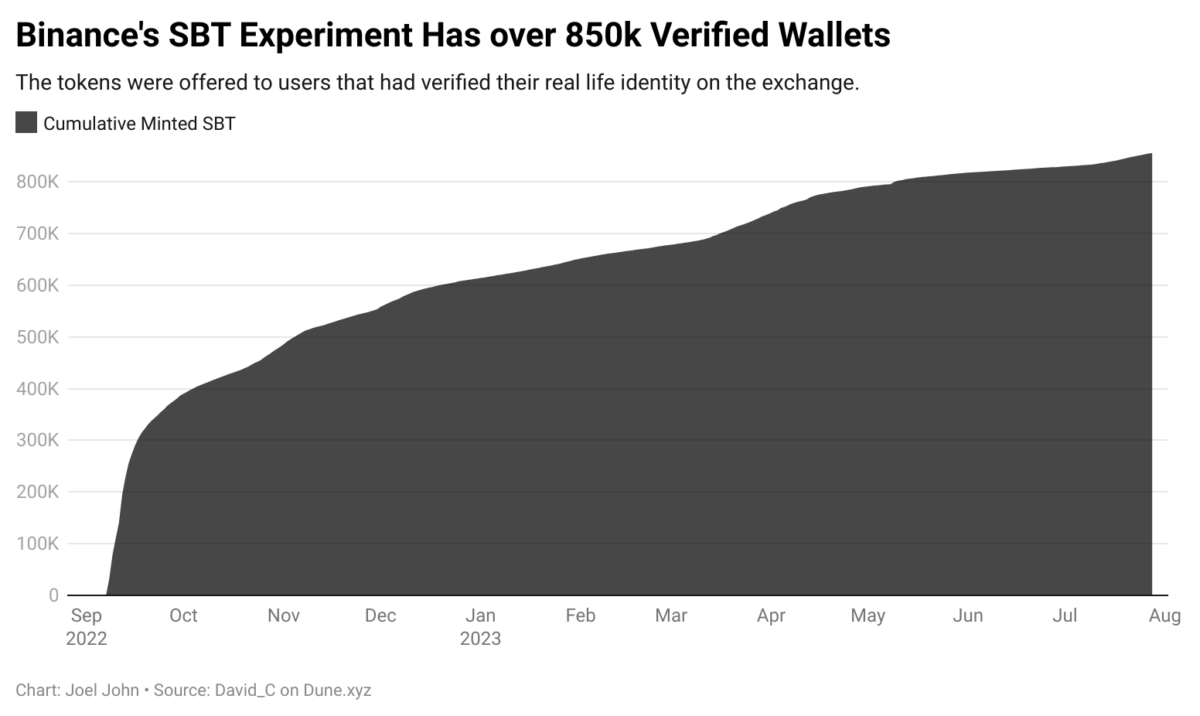
One early instance of an exchange tinkering with on-chain identity is that of Binance’s experiments with BABT. Specifically, a Binance account-bound token is the equivalent of a Soulbound Token (SBT) issued on the Binance Smart Chain. The token was offered to users who had done their AML/KYC on the exchange. Over the past year, over 850k wallets claimed a BABT in an early attempt at creating linkages between wallets and real-life identity at scale.
But why bother with it? It helps applications know that a user is ‘real’. By limiting access to users who have provided their verification documents (in the form of passports or other regional documents), products enabling access to a handful of wallets can optimise for reducing Sybil attacks and increase the number of real users with minimal effect.
In such an instance, the dApp does not access a user’s verification documents. That function is executed by an exchange (like Binance), which may use the APIs of a centralised service provider like Refinitiv. For dApps, the upside is having a verified subset of users who have already proved they are human.
The approaches with which information on a user is gathered and passed on to an app vary depending on the context and resources at hand. There are multiple ways to go about it. Before we get into the models, though, it helps to master a few basic terms. A detailed breakdown of each of these concepts is beyond the scope of this article, but I have attached hyperlinks where relevant for the curious ones amongst our reader base.
1. Self-Sovereign Identity
Think of it as a design philosophy that puts the credential owner in complete control of their identification documents. In traditional, state-sanctioned forms of identity, a government or an institution is responsible for issuing and validating identification.
When a person hands over their identity documents, like a license for verification, the government’s systems must not cut the person off. SSI’s core argument is that a person should be in control of (i) management (ii) privacy, and (iii) access to an individual’s identity.
An SSI-based identity product can contain multiple forms of identity, such as certificates from their university, a passport, driving licenses, and so on. Each of these may be issued by centralized institutions, too. SSI’s core argument is that users should control how these details are accessed.
2. Verifiable Credentials
Verifiable credentials are a model of the cryptographic validation of a person’s identity. At its core, the model is contingent on three parts: an issuer, a verifier, and the credential holder. An issuer (like a university) can issue cryptographic proofs, signed by the organization, to a credential holder. These proofs are used to back what is considered a ‘claim’.
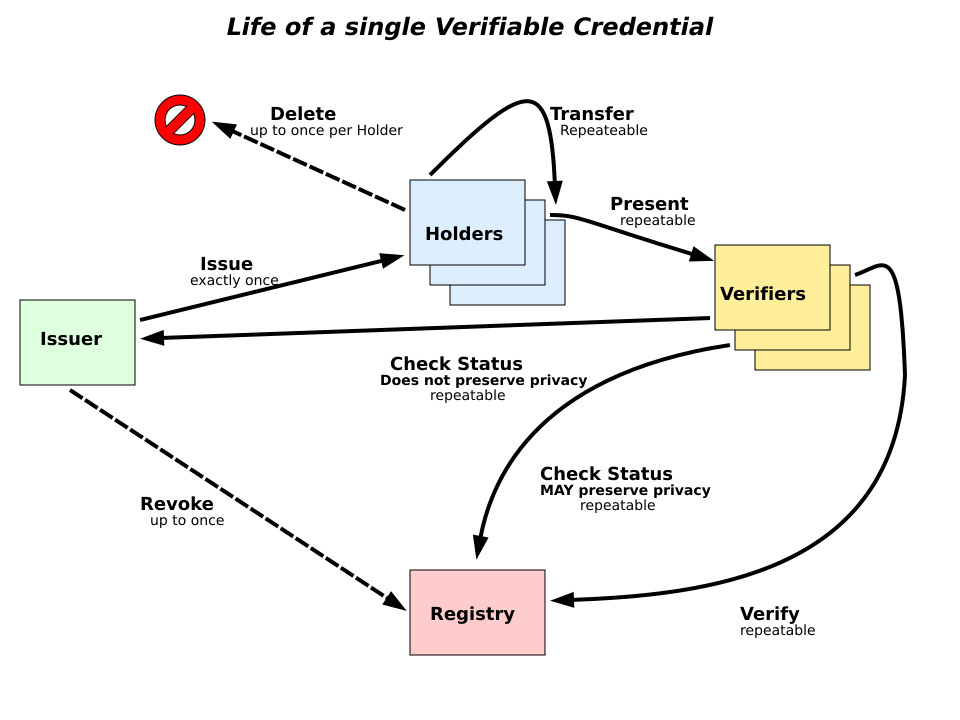
In this context, a claim could be anything, ranging from ‘X studied here’ to ‘Y worked with us for five years’. Multiple claims can be merged to make what is known as a graph of an individual. In the case of a verified credential, the documents (like passports or certificates) are not passed along; only cryptographic signatures from issuers are passed along to validate identity. You can see a live version of such a model here.
3. Decentralised Identifiers
Decentralised identifiers (DIDs) are the structural equivalent of a phone number or an e-mail address for your inbox. Think of it as a wallet address for your identification. When you use a platform that requires you to verify your age or geolocation, providing a DID could help the application verify that you fit the parameters needed to use the product.
Instead of manually uploading your passport to Binance, you could provide a DID. The compliance team at Binance can then validate the location of the proofs held by your DID and onboard you as a user.
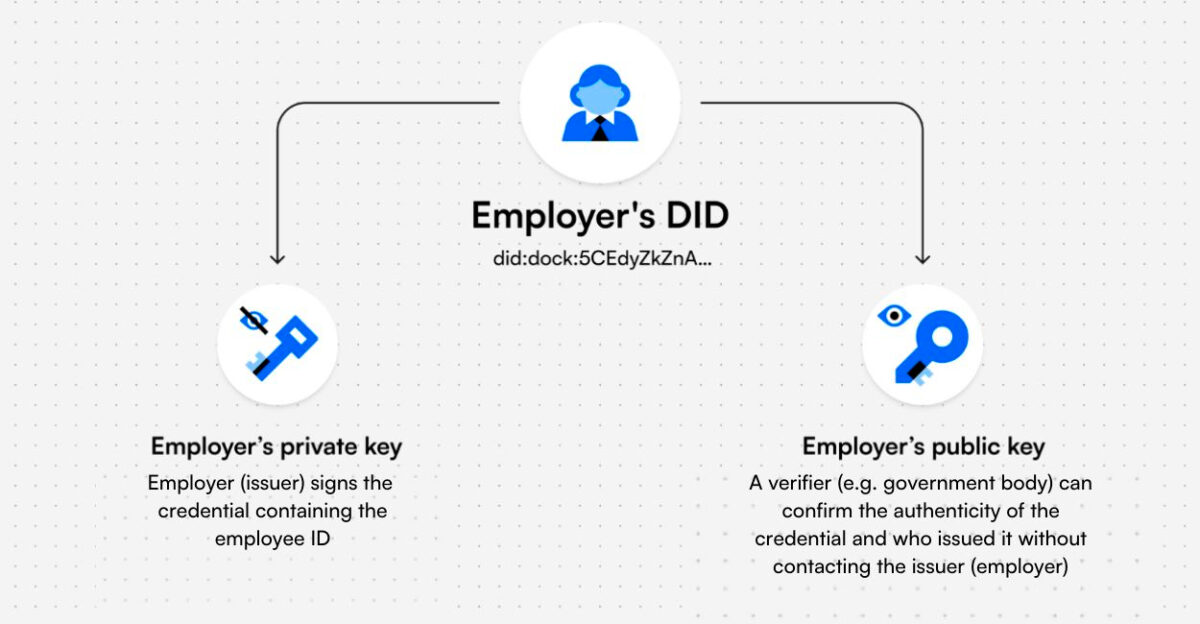
You may have multiple DIDs with segregated identification proofs on each, as you hold separate wallet addresses today. Tools like Dock allow users to hold their identification proofs and authenticate access directly from a mobile app. In this sense, users of blockchain native applications are already accustomed to the flow of signing transactions and verifying the authenticity of an identity request. An alternative approach. An alternative approach to managing segregated forms of identity across wallets is ERC-6551.
Zero-knowledge proofs (ZKP) allow users to prove eligibility without disclosing specifics. Each time I apply for a visa to the UK, I have to provide all my banking transactions for the past quarter. The lack of privacy from a foreign visa administrator going through my banking transactions is not discussed much but it is one of the only ways to get a visa.
Proving you have the funds to travel and return home is a requirement. In a ZKP model, a visa officer could query if a person had a banking balance over a certain threshold for a specific period without seeing all of the person’s bank transactions.
This may seem far-fetched, but primitives that do this exist here and now. zkPass’s pre-alpha was launched in July of this year, allowing users to provide anonymized personal data (alongside verification documents) to third parties via a Chrome extension.
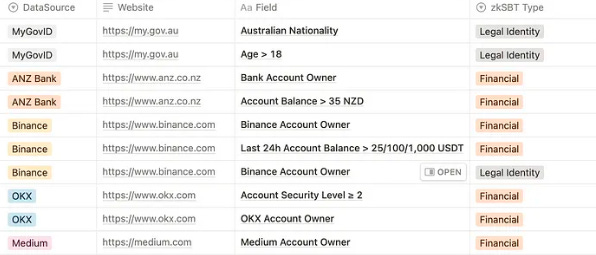
A list of data types supported by zkPass’ Beta product
The range of application support goes from merely proving your identity via a third-party service provider to proving you have learned specific courses on Coursera. They do not host identity-related documents but query them off websites using HTTPS.
Evolving Infrastructure & Use Cases
I could go on all day about the ecosystem of identity-related applications in Web3. Millions of dollars in venture capital have flown to many developers who have delivered over the past few years. However, we are not building a market map of identity solutions here; I want to focus on what the evolution of these identity primitives means for the internet today. A piece by Dani Grant and Nick Grossman from 2018 on USV’s blog gives a good reference for the next phase.
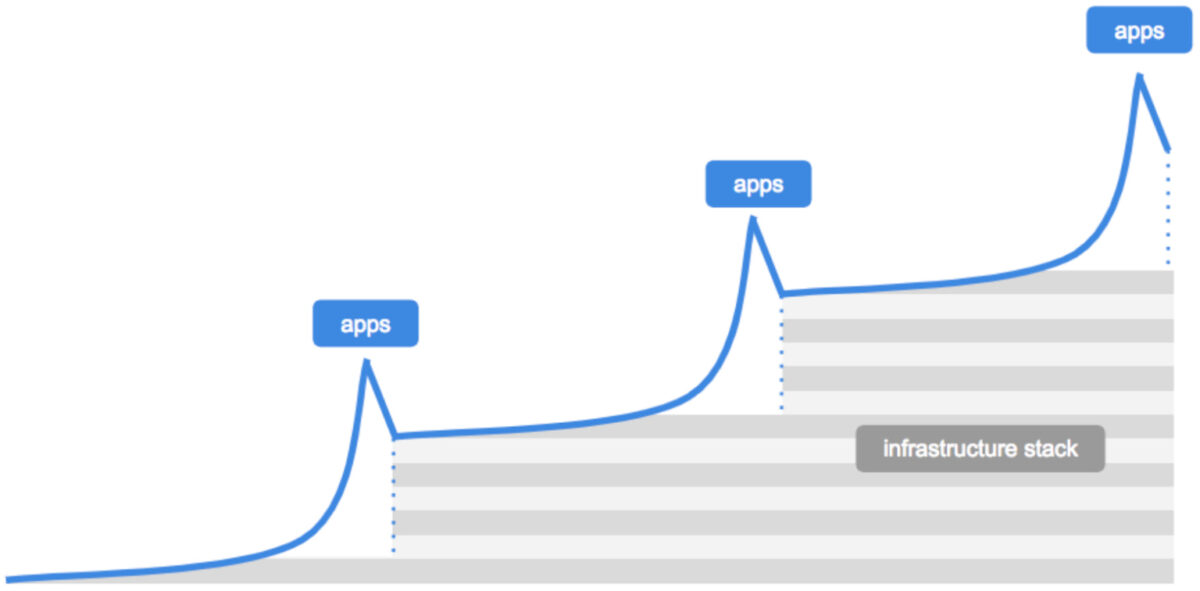
Source: USV
According to them, first comes breakthrough applications requiring better infrastructure. This leads to a point where infrastructure must evolve to support scaling applications. A new generation of applications is then built on this revamped infrastructure layer, and the cycle repeats until a mature market exists – for example, blockchains and NFTs. In 2017, the Ethereum network entirely clogged due to CryptoKitties and came to a standstill.
In 2021, the high price of NFTs justified spending money on NFT transfers. As of 2023, you can send millions of NFTs for less than $100 on Solana, partly explaining why OpenSea has integrated Solana into their product over the years.
Historically, developers had no incentive to tinker with identifying their users. They would have reduced their market size if they had forced users to provide documentation. The law is, in part, what has nudged many developers to implement the identification of users.
Quite recently, Celestia’s airdrop for their token, TIA, prohibited persons from the United States from accessing it. The other reason for verifying the identification of users has been to check for Sybil airdrop farmers. In both cases, emergent networks need primitives to prove who is becoming a participant.
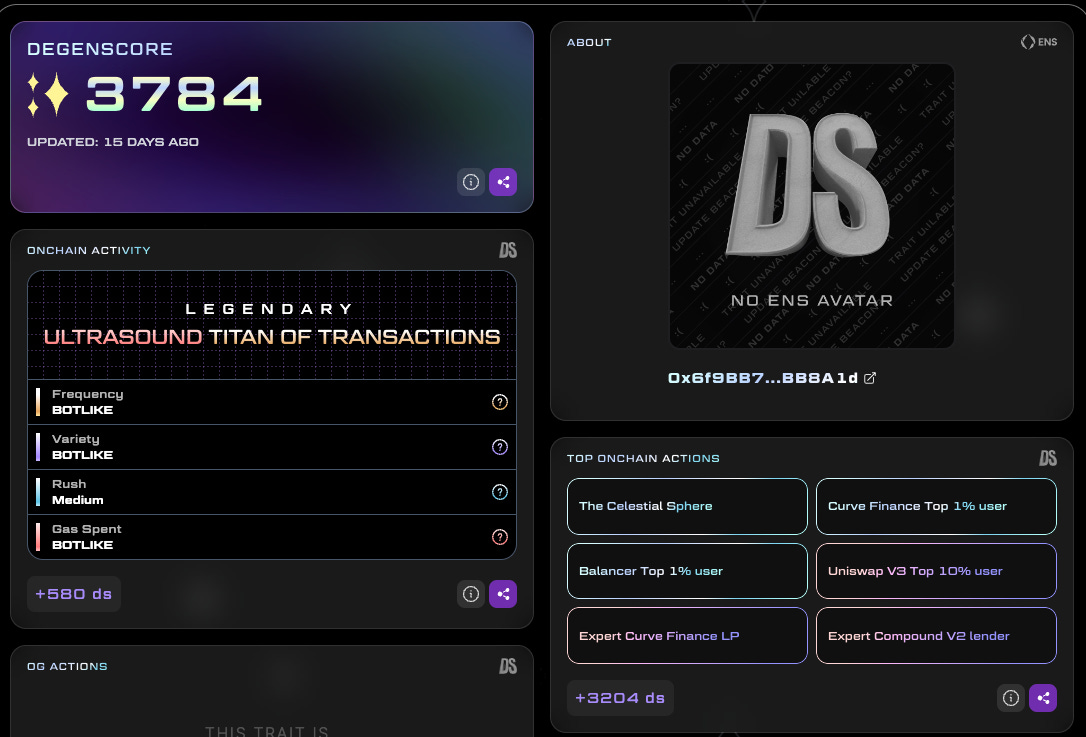
A profile of a user from DegenScore
One of the primitives that has seen substantial adoption in this regard is DegenScore. This product parses a user’s historical data to assign them a score. Apps launched on-chain can then enable access to wallets based on the user’s score. This strategy restricts people from making hundreds of wallets and attacking emerging products for airdrops.
The product is not an identity verification tool in that it does not check whether or not you have a state-issued document. However, it provides a mechanism for developers to validate if users should have access to their products based on their historical behavior patterns.
One product that combines off-chain identity with an on-chain wallet is the Gitcoin Passport. This product assigns ‘stamps’ each time people link a form of identification to their wallet address. The stamps could be given for linking a Facebook account, LinkedIn or Civic ID. Verified credentials are issued from Gitcoin’s servers to a person’s wallet address. As such, the product uses the Ethereum Attestation Service to bring these stamps online.
What’s the point of all this? In Gitcoin’s case, it is primarily used for grants. Given that the product matches donations made for public goods, it becomes vital for the product to verify that real users are donating money. The use case for such a product outside Gitcoin is with DAOs. Oftentimes, a single person could split up his or her tokens across thousands of wallets and vote in favor of a decision that benefits them. In such instances, it becomes essential to validate the personhood of a wallet, either through past on-chain behavior or through linkages with a real-world identity. This is where the Gitcoin Passport is of use.
Naturally, a person will not maintain a single identity in all their applications. It is normal for users to have multiple wallets while using the same product. Consider the number of wallets you may have used with Uniswap. Users also tend to swap wallets depending on the nature of the application they are using.
A separate wallet for gaming, media consumption, and trading is not rare. Products like ArcX Analytics combine browser data (like Google Analytics does) with smart contract interaction data from blockchains to help identify users. They primarily target developers wanting to understand the behavioural patterns of their users.
The tools for handling multiple pseudonymous identities have also been evolving in tandem. ReDefined allows users to resolve their e-mail addresses to a certain wallet owned by them. Their API allows developers to create custom resolvers, which means you can have products where a user’s phone number resolves to a wallet address.
Why does this matter? It makes building a remittance application like Venmo as easy as a few clicks. A user could upload their contact list (like one does with Whatsapp), and a product like ReDeFined could map out all the phone numbers to addresses on-chain.
While writing this piece, I resolved my e-mail address (joel@decentralised.co) to a wallet address. The data on which e-mail is owned by which wallet address is not stored on ReDeFined’s servers. They cannot change it without me signing in from my wallet address, as the resolution data (the bits that match an e-mail to a wallet address) is stored on IPFS.
You can link wallet addresses across chains like Bitcoin, Solana or Polygon on ReDeFined. The product checks which asset is being sent by a user and routes the asset to the wallet on a matching chain.
But what if you wanted to identify and rank users across a protocol like Lens? Ranking algorithms for user behavior have been emerging on Web3 native social networks. In the late 1990s, Google came to be what it is through studying the relative ranking between pages on the internet.
Aptly named PageRank, the system gave reputation scores to websites based on how frequently they were mentioned on other websites. Two decades later, as the web has slowly become composable (through Web3 native social networks), we have the same conundrum with wallets. How do you validate a user’s “value” on one social network using their activity on a different network? Karma3 solves this.
It helps applications (and users) figure out how to rank a community member within a DAO or see which artist’s previous mints were abandoned. As the core unit of identity (the wallet address) is used across protocols, Karma3’s product helps rank wallets. So, a user on the Lens Protocol may not have to start from scratch when writing on Mirror.xyz.
Composable ranking gives products a relative advantage to users with high signals on one product when they port over to a different one.
The ability to port reputation has historically not existed on the internet. You could have 100k followers on Twitter, but when you start on Instagram, you start from scratch. This disincentivizes large creators from switching over to new social networks. This is partly why, despite their relevance and need, Web3 native social networks have not grown to scale yet. The discovery engines are broken, and the incentives to switch to alternatives do not exist.
In a model using Karma3’s products, new social networks do not have to start from scratch when ranking users relatively, solving the cold start problem of attracting good creators early on. Does that mean we will see a multitude of niche-specific social networks emerge? It is well within the realm of possibilities.
So far, we have only talked about individual reputations, specifically about reputation in the context of a person who is active on-chain. But what if you could create composable metadata about firms that could be queried and displayed across outlets? This happens today in a Web2 native fashion. Crunchbase was pulling in details about firms from LinkedIn as early as 2008.
The problem is that nothing stops Crunchbase, in this example, from falsifying data shown by them on a third-party outlet. You can ‘trust’ the system because, in this hypothetical model, an outlet (like Crunchbase) has every incentive to relay accurate information. However, the corporate entity is not in control.
This matters, especially in the context of Web3, as traders often make decisions based on details they find on Messari, CoinGecko, or CoinMarketCap. The Grid is creating a network of verifiable credentials for firms. In their model, a firm could use its private key to upload details, such as investors, team members, funds raised, logos, and so on, to a sufficiently decentralised network.
Third-party data platforms, such as VCData.site, could query information from The Grid to show it to users. The advantage of such a system is that a firm would not have to go across multiple platforms to update its details. Any time a venture updates its details using verified credentials, it would be reflected on all platforms that query its data.
(Sidenote: The Grid’s founder had previously built a company in the data space and sold it to CB Insights. So I’d like to think he knows what he’s doing. Do slide into his DMs on Twitter if the theme interests you).
Third-party verifiers (like community members) would be incentivized to dispute falsified claims on such a network. It is still theoretical and far-fetched, but the ability to have a unified update on all information related to a venture across all platforms that mention it could be powerful.
But what applications could such reputation primitives enable? A fairly simple instance could be loans in the context of real-world asset (RWA) lending.
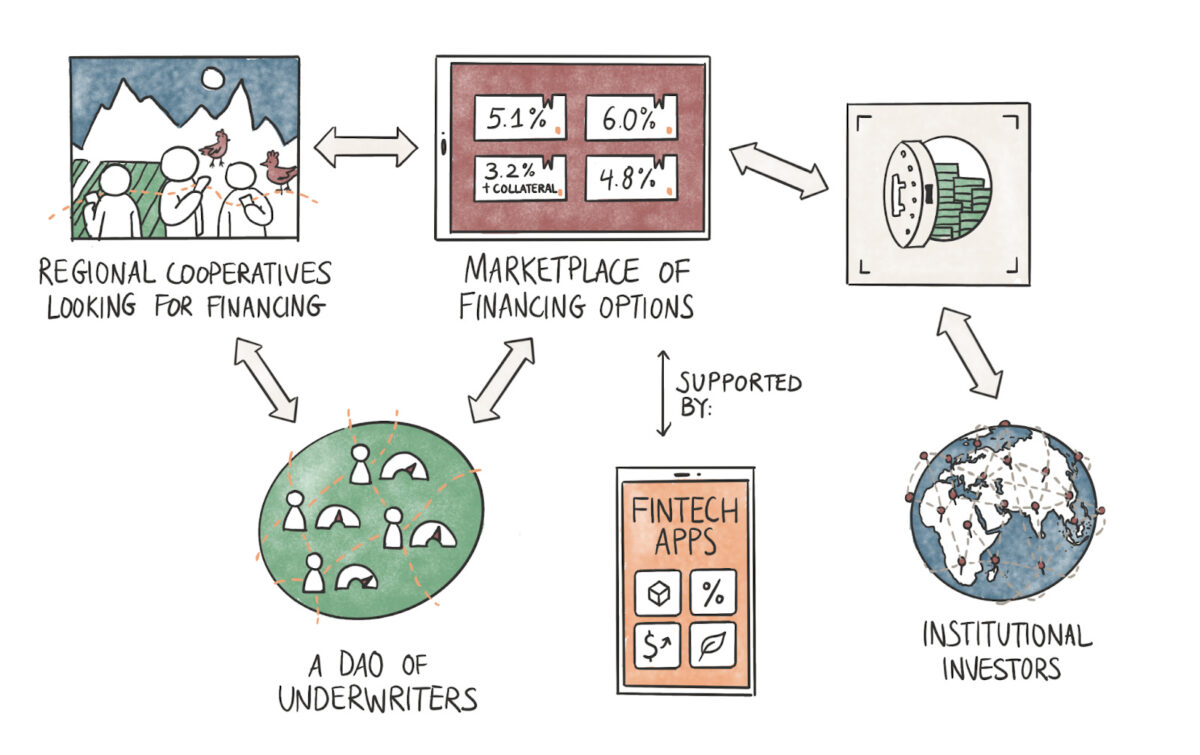
The flow above shows what that could look like in practice. Grameen Bank has made a reputation for being the go-to bank for cooperatives in the emerging world. Part of the reason is the social reputation attached to a person defaulting on a loan. Cooperatives, consisting of women engaged with SMEs, take loans directly from the bank and keep a rotating line of credit that grows depending on the frequency of repayments.
In the 1980s, when digital identities were not common, offering credit to the underbanked with no collateral was revolutionary. In the 2020s, the model could evolve with the digital primitives we do have.
In the image shown above, cooperatives could provide their data to underwriters that function as DAOs. This data would primarily involve their banking details, the SME’s commercial transactions, and similar data points from Web2 native products. Tools like zkPass (referred to above) could anonymise and provide the data to underwriters, who then could assess the creditworthiness of the cooperatives and pass on a risk score to a marketplace.
The marketplace could source liquidity from fintech apps or institutional investors looking to generate yields on their idle assets. There are two ways this could work:
- A fintech app could directly offer loans to cooperatives with credit scores passed on by an external underwriter.
- An aggregator (or marketplace) could source liquidity from third-party fintech apps or institutional investors and offer loans on the basis of the credit scores provided by an underwriter.
In both instances, cryptographic primitives could be used to ensure the privacy of data provided by borrowers. A DAO, run by multiple underwriters, could help facilitate loans faster than a traditional entity if multiple individuals are racing to assess the risks. Lastly, one could presume that using blockchain rails to source liquidity from global markets could translate to better interest rates for borrowers. Our friends at Qiro have been tinkering with such a model.
While the money flow could vary, the ‘core’ difference is how the underwriting is done and how that score is passed to marketplaces. A cooperative seeking a loan would have to provide their details only once, and they would have the right to protect their personal banking details from third parties that should not have access to them.
Naturally, this is not a crypto product. It is a fintech primitive that uses blockchain technology. The blurring of lines between the two has not historically happened due to regulatory restrictions and the lack of identification on the internet. The nature of applications that can be built on-chain will grow exponentially in sophistication and adoption as the primitives we use to track and identify users evolve.
There are two clear cases where this blurring of lines is already happening. First, with Paypal’s integration of stablecoins in the product. Secondly, with MoneyGram releasing a native wallet in their product. We don’t entirely know what kind of fintech applications could be built as the next hundreds of millions of users come on-chain.

Alexa, play country roads, take me home.
The part of India I come from (Kerala) is known for its beautiful mountains marked by long, winding roads. Local lore has it that when the British came to colonise, they did not know the ways around the mountains and hills. So, they bribed local tribesmen with gifts. Once they learned the routes, the tribesmen were often killed. Many winding roads in Kerala have giant trees with locks as part of local rituals to avoid hauntings on the roads centuries later. It is believed the ghosts of the tribesmen used to cause accidents for passersby on the roads. (I don’t quite believe in the tale, but these stories become a core part of your childhood if you spent your summers in hills like the one above).
What does this story have to do with a blog that covers decentralisation? I think the discovery of a new route is often followed by commerce and then by varying degrees of violence. Violence is often done to ensure faster, more secure means of conducting commerce. (You wipe out the competition.) The “violence” we saw was not physical when the internet came along. It was the subtle invasion of our minds and private spaces through surveillance capitalism. The average user does not know how we pass our data on behemoths on the web.
Do I think all of them would come over to Web3 native identification primitives? No. But I think, with the efficiencies of speed, cost & transparency blockchains offer, we can offer superior products. The ecosystem could expand as Web3 native products like zkPass and Soul Bound Tokens make their lives easier with the pace at which identification can occur. Users will inevitably realize that an alternative model exists where they can choose not to give their personal information to strangers on the internet. That moment of realization is likely when the internet evolves.
Many of us did not start with strong views on decentralisation. Some of us used Bitcoin and saw how quickly it sent money across the planet. The journey for the following hundred million users might be the same when it comes to identity and data-related primitives. If we build products that are meaningfully better, they will switch over to Web3 native alternatives that put the user in control of their data.
What excites me is the nature of consumer-facing applications that may come from this next wave of “identified” users. It is a long-winded pathway before we map clusters of users on-chain. But the primitives to help with those transitions are here and now. Technology empowers users to a point where violence against them can no longer be conducted.
We will be covering applications & business models that these identity primitives would enable in another piece.
– Joel
[This article has been written and prepared by Joel John, Siddharth, and published by the GCR Research Team, a group of dedicated professionals with extensive knowledge and expertise in their field. Committed to staying current with industry developments and providing accurate and valuable information, GlobalCoinResearch.com is a trusted source for insightful news, research, and analysis.]
Disclaimer: Investing carries with it inherent risks, including but not limited to technical, operational, and human errors, as well as platform failures. The content provided is purely for educational purposes and should not be considered as financial advice. The authors of this content are not professional or licensed financial advisors and the views expressed are their own and do not represent the opinions of any organization they may be affiliated with.